
New Hampshire Cyber Threat Assessment
Introduction: CISO’s view of the world over the next two years
This Cyber Threat Assessment is based on discussions while walking around the State and interacting with IT professionals, risk managers, organizational leaders, managed service providers, and experts in the private sector in a variety of individual and group settings. It is also informed by close collaboration with the other 54 State and Territorial Chief Information Security Officers (CISOs) across the country. Unclassified threat intelligence shared by public and private sector partners, and other open sources of cyber threat information and intelligence, were used in the obvious places. Basically, I just did a bunch of Google Searches to find recent examples that fit the various sections of this paper. This Threat Assessment also leverages extensive work done by the New Jersey Cybersecurity and Communications Integration Cell (NJCCIC).
This threat assessment is meant to give you a working knowledge without having to read too much at once or read about these things every day. It also describes some significant incidents, profiles of threat actors, systemic risks and emerging technologies in a way that can be understood by those who are not cybersecurity professionals to inform better cybersecurity outcomes across New Hampshire.
Bottom Line up Front (BLUF)
New Hampshire faces an evolving cyber threat landscape, characterized by cyberattacks that can be launched from anywhere in the world at any time of day or night.
- The most likely things users/administrators will see are phishing emails, attacks to compromise identities, business email compromise to enable good old-fashioned grifting, and ransomware attacks.
- Both public and private sector organizations are highly likely to be victims of cyberattacks, requiring robust security measures and proactive threat mitigation.
- Nation-state actors, cybercrime organizations, hacktivists, and others with diverse motivations and considerable technical capabilities pose significant threats.
- Unmitigated cyber risk can result in disruptions and cascading failures across critical infrastructure sectors, requiring collaborative efforts to build resilience and enhance preparedness.
- The rapid evolution and adoption of emerging technologies, such as artificial intelligence, necessitate continuous adaptation and innovation in cybersecurity practices.
The Threat Environment
New Hampshire's public and private sector institutions, as well as its residents, face a pervasive and credible threat of cyberattacks from multiple types of threat actors with varying capabilities and motivations. Nation-state actors, such as China, Russia, Iran, and North Korea have targeted American companies and infrastructure for espionage and potential disruption of critical systems. Transnational cybercrime organizations, such as LockBit, cl0P, and BlackCat/AlphV, continue to conduct financially motivated ransomware attacks on all manner of organizations, including hospitals, local governments, law enforcement agencies, large and small businesses, and educational institutions.
Hacktivist groups that are motivated by political, religious, and other causes and ideologies have demonstrated their ability to cause outages through disruptive distributed denial-of-service (DDOS) attacks and their ability to gain unauthorized access to systems that are used to manage energy and water systems. In 2023, KillNet, a hacktivist collective aligned with the Kremlin in Russia carried out numerous DDOS attacks against public and private sector organizations as retribution for their respective countries’ support of Ukraine. These DDOS attacks targeted websites and other online services provided by airports, state and federal governments, and hospitals across the United States. KillNet is only one of numerous hacktivist groups that have launched cyberattacks against public and private sector entities in relation to both the Russia-Ukraine and the Israel-Hamas wars.
The 2021 Colonial Pipeline ransomware attack disrupted fuel supplies across the Southeastern portion of the United States for days. The 2020 SolarWinds supply chain attack compromised thousands of public and private sector entities. In May 2023, a mass exploitation of a vulnerability in approximately 2,100 MOVEit file transfer servers worldwide resulted in the exfiltration of personal information of over 60 million individuals. In October 2023, a vulnerability in the remote access appliance software of Citrix NetScaler products, dubbed Citrix Bleed, allowed threat actors to mass exploit the networks of companies and organizations around the world. The impact of this mass exploitation closed Australia’s shipping ports for days, resulted in the breach of sensitive personally identifiable information (PII) of approximately 36 million Comcast customers, and forced hospitals across the United States to divert patients from their emergency rooms, postpone surgeries, and use paper-based processes, thereby slowing patient care.
These and other incidents highlight how cyberattacks are not constrained by geographic borders and such attacks can result in cascading impacts across industries, regions, and the world. The nature and consequences of these examples demonstrate how cyberattacks can affect New Hampshire now and in the future.
Incident Reporting is Everyone’s Responsibility
If you work in State Government, it is very important to report a suspected cyber incident to the DoIT helpdesk via email or phone as follows:
- Email: helpdesk@doit.nh.gov
- Phone: (603) 271-7555 (Outside of 7:30 AM to 4:30 PM, dial the same number and select “Option 2")
If you are a New Hampshire City, Town, County, Police Department, Fire Department or K12 and a member of the New Hampshire Public Risk Management Exchange (PRIMEX) who suspects a cyber incident has occurred, contact PRIMEX immediately to open a claim and get the dedicated cyber first responders engaged.
If you are part of an organization that is not a member of PRIMEX, or are a private entity and you suspect an incident has occurred, contact the New Hampshire Department of Safety’s Information and Analysis Center at Report a Cyber Incident or at nhiac.cyber@dos.nh.gov.
Compromised Login Credentials as an Attack Vector
According to the 2023 Verizon Data Breach Report, up to 80% of all breaches are the result of stolen or otherwise compromised login credentials (usernames and passwords). Compromised login credentials are a favored method for threat actors to gain unauthorized access to networks, often without detection, by appearing as legitimate logins. Various reports estimate there are over 6.7 billion sets of compromised credentials available on the internet. Identity-based attacks are expected to remain the fastest growing method of attack for threat actors targeting New Hampshire public and private sector organizations, as well as the State’s residents and businesses, in 2024.
Threat Actors – The “Bad Guys and Gals”
“Threat actor” is a broad term used to describe any individual or group that conducts a malicious cyber act against a person or organization.
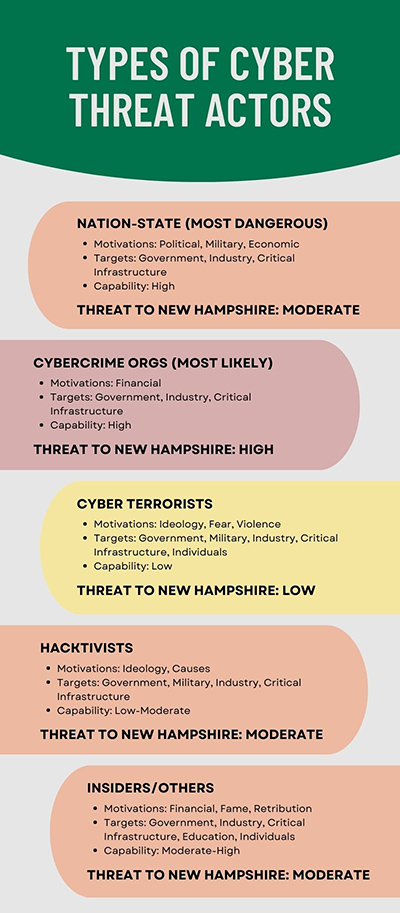
They include nation-state threat actors, cybercrime organizations, hacktivists, cyber terrorists, and insiders/other threat actors. These threat actors are responsible for the majority of significant cyberattacks and pose the greatest threat to New Hampshire and the nation. While each group has some unique characteristics, it is often difficult to discern the true alignment of cybercrime syndicates, hacktivists, and cyber terrorists, as they may covertly act on behalf of, or in support of, nation-state interests despite appearances of independence. There are a couple places I use an industry term: APT-XX. APT is Advanced Persistent Threat: an entity that is good at what they do, is sneaky about it, and is in it for the long-term. A summary of threat actor types is described in Figure 1.
Nation-State Threat Actors – The Most Dangerous Threat
Nation-state threat actors are threat groups that are working in support of, or directly for, a government body/state organization, such as an intelligence service to further their geopolitical, military, or economic objectives. They are generally well resourced and utilize advanced tools, techniques, and procedures to execute stealthy and long-term operations at the direction of, or on behalf of the state. China, Russia, Iran, and North Korea are typically considered the four primary nation-state threat actors that present the greatest and most persistent threats to New Hampshire and the nation. They are skilled at using cyber operations to further their strategic goals through various techniques, including espionage against government and industry targets, prepositioning malware on critical infrastructure networks for future operations, building networks of compromised devices across the world to enable malicious activity, executing highly disruptive cyberattacks on infrastructure and businesses, and engaging in information operations to spread propaganda and disinformation.
China
China is one of the most capable and persistent nation-state cyber threats. China's cyber operations are led by the Ministry of State Security (MSS) and the People's Liberation Army's (PLA) to conduct global cyber espionage operations and steal intellectual property to support China's economic and military modernization. Key targets include political, economic, military, and critical infrastructure networks. China-linked groups have become known for sophisticated, stealthy intrusions designed to silently gather intelligence for the long term.
In July 2023, Volt Typhoon, a threat actor group affiliated with the PLA, compromised nearly two dozen critical infrastructure organizations, including organizations in communications, manufacturing, utility, transportation, construction, maritime, government, information technology, and education across the United States. To evade detection, Volt Typhoon employed stealth techniques, such as leveraging compromised small-office/home-office (SOHO) devices to disguise the origin of their activity and using tools readily available on the Internet (these are called “living off the land” (LOTL) tools) for discovery and lateral movement across networks. Their activities have been linked to the theft of classified information and intellectual property from organizations in the targeted industries.
Other notable state-sponsored threat actor groups affiliated with China’s government, military, and intelligence services include Hafnium, Storm-0588, and APT-41. Hafnium is responsible for exploiting previously unknown Microsoft Exchange Server vulnerabilities in early 2021 to compromise tens of thousands of organizations globally. In July 2023, Microsoft and United States officials reported that the Chinese State-linked threat actor Storm-0558 gained unauthorized access to Microsoft365 email accounts at 25 federal government organizations, including the US Department of Commerce and the US Department of State. At least 60,000 emails were exfiltrated during the attack. APT-41, another Chinese Cyber Organization, has been conducting both state-sponsored targeted intrusions that often align with Chinese Communist Party (CCP) objectives, as well as criminally focused operations, since at least 2014. In 2020, the United States Department of Justice indicted seven individuals linked to APT-41 for their roles in hacking, identity theft, money laundering, and wire fraud crimes. More recently, APT-41 has been linked to the theft of more than $20 million in United States COVID-19 Economic Relief benefits. These four groups represent only a small fraction of China’s state-sponsored cyber threat apparatus. As China continues to use these groups to support its long term economic and military goals, they are a highly capable and well- resourced cyber threat (APT) to New Hampshire in 2024 and beyond.
Russia
Russia is one of the most formidable and aggressive nation-state cyber threats. Russian cyber operations are primarily conducted by intelligence services, such as the Federal Security Service of the Russian Federation (FSB), the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU), and the Foreign Intelligence Service of the Russian Federation (SVR) often targeting government, military, diplomatic, and other organizations and businesses worldwide for intelligence that benefits Russia’s foreign policy and military decision-making. Russian state-sponsored cyber actors are skilled at developing custom malware and exploiting previously unknown vulnerabilities in software to target government, military, and private sector networks globally.
Over the past several years, several debilitating and destructive cyberattacks have been attributed to GRU. In December of 2015, GRU operatives, referred to as Sandworm, launched cyberattacks against Ukraine’s power grid, resulting in power outages for hundreds of thousands in the Kyiv region. The malware used to disable the power grid also wiped and destroyed files on infected computer systems. In 2016, GRU refined their malware and automated their cyberattacks against Ukraine’s power grid causing more power outages. In 2017, GRU inserted malware into an accounting software update that resulted in the most damaging cyberattack in history. Although the malware was intended to target and cripple businesses operating in Ukraine, its destructive nature spread worldwide. This cyberattack is known as NotPetya and resulted in over $10 billion of damages. As with the Ukraine power grid attack, the malware used in NotPetya infected and wiped computer systems. In 2020, the US Department of Justice indicted six GRU officers for their roles in the Ukraine power grid and NotPetya attacks, as well as several other cyberattacks.
In late 2020, the cybersecurity firm Mandiant discovered it had been the victim of a sophisticated espionage-focused software supply chain attack that was later attributed to the Russian SVR group, APT-29 (aka, Cozy Bear), which leveraged a back door in SolarWinds’ Orion network management software to breach numerous US government agencies, critical infrastructure entities, and major technology companies. These victims included the US Department of Defense, the US Department of Treasury, the US Department of Homeland Security, Microsoft, Cisco, Palo Alto Networks, and many others. The fact this trojan horse remained undetected for almost 14 months demonstrates the capabilities of Russian state-sponsored threat actors to stealthily infiltrate their targets’ networks. The SolarWinds incident also demonstrates that nation-state groups will exploit trusted technology supply chains and service providers to obscure attribution and enable widespread access. The SolarWinds hack exemplifies systemic risks from third party products that will continue to threaten New Hampshire public and private sector organizations.
Furthermore, as evidenced during the 2016-2020 US presidential campaign cycles, Russian state-sponsored threat groups present a threat to candidates’ campaigns, national campaign committees, and state and local election infrastructure. With the 2024 US presidential election in November, New Hampshire should expect widespread misinformation campaigns by Russian operatives.
Iran
Iran poses a significant cyber threat to New Hampshire, as evidenced by recent indictments and global cyberattacks. In September 2022, the US Attorney’s Office for the District of New Jersey charged them with engaging in computer intrusions and ransomware-style extortion against US critical infrastructure providers, small businesses, government agencies, non-profit programs, and educational and religious institutions. The indictment revealed that the defendants' hacking campaign exploited known vulnerabilities in network device software, causing damages and losses to the victims.
In November 2023, water and wastewater utilities nationwide were targeted in a series of cyberattacks attributed to CyberAv3ngers, an Iranian-backed group. In these incidents, the threat actors compromised Unitronics programmable logic controllers (PLCs) used mainly in the Water and Wastewater sector but also implemented in other industries, including Energy, Food and Agriculture, and Healthcare and Public Health. CyberAv3ngers claimed responsibility for over a dozen cyberattacks launched since October 30, 2023, stating that they targeted Unitronics as it is Israeli-made and “Every equipment ‘made in Israel’ is CyberAv3ngers legal target.” These incidents are evidence of the active and ongoing threat posed by Iran in the cyber domain to New Hampshire's critical infrastructure and businesses.
North Korea
North Korea is one of the United States’ top cyber adversaries, however, they often operate differently than other nation-state threat actors. North Korea leverages cyber capabilities in the same manner as cyber criminals to generate revenue and retaliate against the enemies of the Hermit Kingdom. In 2023, the theft of over $600M in cryptocurrency was attributed to North Korean state-sponsored threat actors. For North Korea, it’s “Show me the Money.”
North Korean cyber operations are conducted by the intelligence bureaus, such as the Reconnaissance General Bureau. Prominent North Korean threat groups, including the Lazarus Group and APT-38, carry out cyber operations worldwide. In 2014, Lazarus Group hacked Sony Pictures in retaliation for releasing the film The Interview, wiping data, and leaking internal documents. In 2016, APT-38 stole $81 million from the Bank of Bangladesh. In 2018, the US Department of Justice attributed the May 2017 WannaCry ransomware attack that infected over 300,000 computers in 150 countries to North Korea. Over 70,000 computers in hospitals operated by the National Health Services in the United Kingdom were encrypted because of the WannaCry attack, impacting hospital operations and patient care throughout England and Scotland. Additionally, the WannaCry malware spread to and impacted numerous computer systems in the United States. These examples underscore the ongoing and evolving cyber threats posed by North Korea. Its ability to target healthcare and financial entities and launch debilitating and costly cyberattacks, such as the Sony Picture hack and WannaCry, makes North Korea a threat to New Hampshire organizations in these sectors and beyond in 2024.
Cybercrime Organizations – The Most Likely Threat to New Hampshire
Cybercrime organizations are sophisticated criminal organizations that leverage digital technologies to carry out illegal activities, primarily for financial gain. These activities include ransomware attacks, financial fraud, intellectual property theft, identity theft, and the sale of illegal goods and services on the dark web. These syndicates are often characterized by their hierarchical and compartmentalized structure and are often organized like a typical business with clear divisions of labor among members who may possess specialized skills in hacking, social engineering, money laundering, and other cybercrime techniques. They continuously adapt their tactics to avoid detection, employing encryption and anonymizing tools.
The global nature of these organizations poses significant challenges to law enforcement, as they often operate in jurisdictions with weak cybersecurity laws, limited resources for cybercrime investigations, and, in some cases, implicit or explicit permission of authorities. Even when law enforcement successfully shuts down their operations, they are quick to reconstitute, rebrand under another name, and get back to business.
Notable ransomware groups (and impacted victims) over the past several years include LockBit (Capital Health), BlackCat/AlphV (Caesars and MGM), Darkside (Colonial Pipeline), etc. In February 2022, the Conti ransomware group pledged its full support to Russian President Vladimir Putin and the Kremlin, and further blurred the lines between criminal- and state-sponsored activities. The worldwide reach of cybercrime syndicate operations poses an ongoing and significant threat to New Hampshire public and private sector organizations, as well as New Hampshire residents. Their attacks cause substantial economic damage and threaten personal health, safety, and privacy on a global scale.
Hacktivists – New Hampshire may see this…depending on the “Cause.”
Hacktivist groups use hacking techniques to promote social or political agendas and ideologies. These groups believe they can affect change and feel justified in targeting individuals, organizations, or government agencies in support of their beliefs and allegiances. In response to the Russia-Ukraine and Israel-Hamas wars, numerous hacktivist groups have emerged targeting the infrastructure of their side’s adversaries as well as those adversaries’ allies.
For example, KillNet is a collective of members and volunteers who support Russian geopolitical ideology and began operations around March 2022 in support of Russia’s invasion of Ukraine. The group has since conducted numerous DDOS attacks targeting government institutions and private companies directly and indirectly supporting Ukraine’s war efforts. In addition, KillNet has also targeted the US Healthcare and Public Health sector with DDOS attacks, including New Hampshire’s Dartmouth Health, and the websites of New York and Philadelphia airports. In addition to KillNet, many other hacktivist groups have carried out cyberattacks in support of Russia’s war efforts, including NoName057(16), Usersec, and Anonymous Sudan. (Don’t ask me where they get these names!)
Since October 7, 2023, pro-Hamas hacktivist groups, some affiliated with Hamas, Hezbollah, Iran, and other Palestinian groups, have launched numerous DDOS attacks against entities in Israel, as well as government and private sector organizations around the world that support Israel. As with the DDOS attacks launched by Russian hacktivists, their impacts last for only a short period of time – hours to days – before the targeted sites recover. Beyond just DDOS attacks, these hacktivist groups have also carried out more nefarious attacks, such as hacking the industrial control systems of energy and water providers; exfiltrating and leaking sensitive information of government, healthcare, and military targets; and infecting targeted systems with wiper malware, resulting in debilitating operational impacts and significant financial losses for their victims.
As with cybercrime syndicates such as Conti, the role and intentions of hacktivist groups are sometimes blurred as their activities may also be state-supported and sponsored. While the DDOS attacks initially launched were simply a nuisance to their targets, they have improved their tradecraft and capabilities over time and now pose a more significant threat.
Cyber Terrorists – Don’t Believe What You See in the Movies!
Cyberterrorists, like hacktivists, use cyberattacks to advance their ideological agendas. Some cyber terrorists are nation-state actors; others act on their own or on behalf of a non-government group. To date, traditional foreign and domestic terrorist groups that use violence to achieve their goals have not demonstrated the advanced capabilities necessary to carry out significant cyberattacks. However, some of the hacktivist groups, who claim to be carrying out cyberattacks in support of their ideologies and causes, may also be members of and proxies for terrorist groups.
Insiders and Other Threat Actors
Beyond the groups listed above, there are other loosely organized threat actor groups, such as Lapsus$, and other unaffiliated individuals, which pose significant threats. Lapsus$, which was active in 2022 and 2023, was made up of mostly teenagers from the United Kingdom, Brazil, and elsewhere. Lapsus$ members were responsible for hacking into some of the most cybersecure and valuable companies in the world, including Microsoft, Nvidia, Samsung, LG, and Uber. In the summer of 2023, British authorities arrested several members of the group who have recently been convicted for their crimes. Other members of Lapsus$ remain free. Lapsus$ often used social engineering and the recruitment of insiders to help carry out their attacks, highlighting that initial access into otherwise secure networks may be accomplished via people and process vulnerabilities instead of technical vulnerabilities.
Lapsus$’s exploits demonstrated that almost anyone with some technical and people skills, an Internet connection, time, and motivation can successfully carry out attacks, even against very secure targets. These loosely formed groups and unaffiliated individuals, like the other major threat actor groups, also pose threats to the public and private institutions and the residents of New Hampshire.
Threats may be Amplified by Emerging Technology
The rapid evolution and adoption of emerging technologies, such as AI, present both unprecedented opportunities and complex challenges, significantly impacting the cybersecurity landscape in 2024. In the near-term, threat actors will use generative AI to produce highly convincing and personalized phishing content at scale, increasing the likelihood that a user will “click.” Additionally, generative AI enables the creation of realistic yet entirely falsified audio and video content. Deepfakes are regularly used in sophisticated impersonation schemes for fraud, extortion, and disinformation campaigns. The distribution of deepfake multimedia content on social media and other platforms will likely be used by threat actors to sway opinions, encourage divisiveness, undermine political candidates and their campaigns, create the perception of a lack of integrity of the election process, and damage the reputations of governments, organizations, and individuals. There is already evidence that threat actors are using AI to develop malware and leverage AI to discover vulnerabilities and optimize targeting. While these use cases are in their infancy, it is highly likely that over time, AI will be used to amplify the capabilities of threat actors and the potential harms they can cause.
While AI may bring societal benefits, their wide availability and low (zero) cost of use also enables threat actors to weaponize these technologies. AI and machine learning in critical systems introduce new attack surfaces open to exploitation. Threat actor techniques, such as data poisoning or evasion attacks, can manipulate AI models to misclassify malicious inputs or generate content that bypasses defenses. Autonomous vehicles, drones, robotics, and control systems in critical infrastructure that use AI for their operation and decision-making could be compromised to cause physical damage. These types of attacks are not likely to be common in New Hampshire, but their use will grow over time.
Systemic Cyber Risk
In our current technology environment, a seemingly isolated system failure or compromise of an individual system can have cascading affects well beyond the initially affected system. Key systemic risks created by insecure software platforms, lack of visibility into third-party networks, and open supply chains create opportunities for threat actors to compromise systems and cause cascading effects. Systemic risk is amplified by the proliferation and dependencies on IT across all facets of society. The integration of embedded and networked technologies into physical devices used by governments, organizations, and individuals create vulnerabilities that are prone to malicious activity, malfunction, human error, and acts of nature. When is the last time you did a project that did not have an IT component or was not dependent on IT? It’s all (mostly) interconnected somehow!
Conclusion
Based on an analysis of cyberattack trends and emerging threats; the motivations, capabilities, and targeting by the various threat actor types; geopolitical issues; and systemic cyber risks, the State of New Hampshire will continue to see cyberattacks against towns, cities, counties, critical infrastructure, health care organizations, K12 schools, higher education, and even individuals. Most of these attacks will be from Cybercriminals and motivated by financial gain, but will still result in degradation of government services, financial loss, and disruptions to our normal way and pace of life. These attacks, although financially motivated, may have second-order effects or unintended consequences that also adversely impact public health, the welfare and safety of our residents, the economy and public interests of the State.
It is unrealistic to expect any one organization to defend against nation-state actors, criminal syndicates, hacktivists, cyber terrorists, and other threat actor groups who can launch attacks from anywhere in the world at any time of day or night. Effectively managing cyber risk requires a proactive and collaborative approach across New Hampshire. Public and private sector organizations at the federal, state, and local levels, as well as businesses large and small, must collaborate to share information, practice good cyber hygiene, implement cybersecurity best practices, and build a culture of cybersecurity awareness and vigilance.



